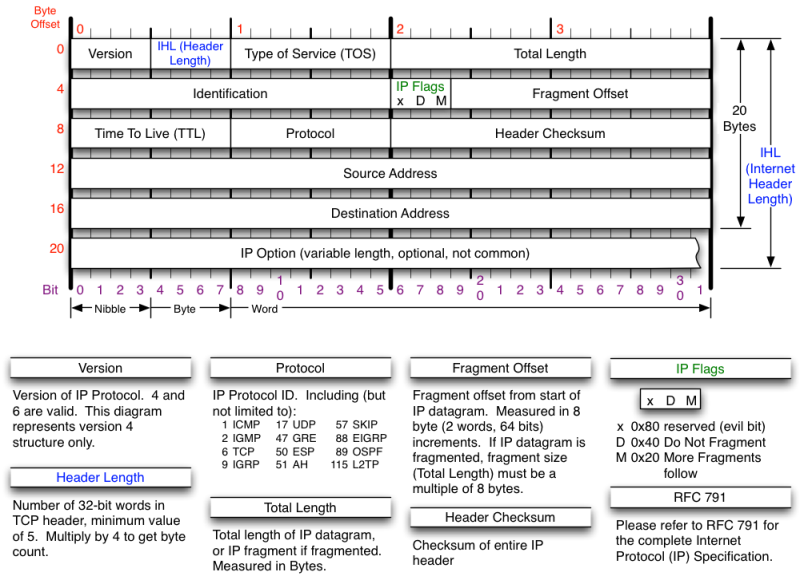
TCP header
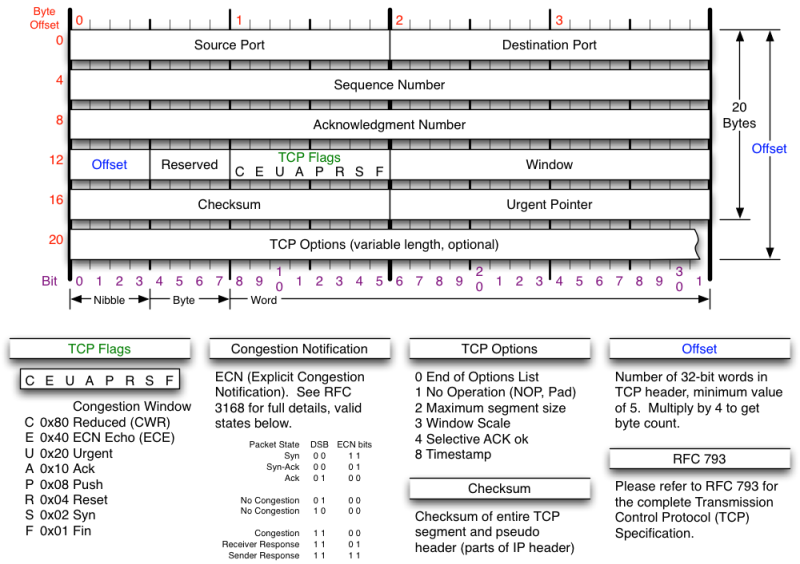
UDP header
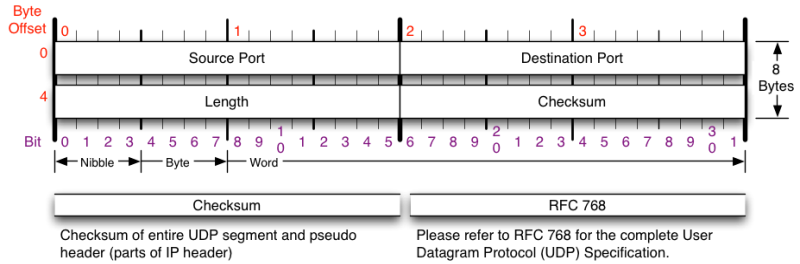
ICMP header
http://nmap.org/book/tcpip-ref.html
Penetration Testing, Vulnerability Assessment, Malware Analysis, Reverse Engineering, Packet Analysis, Wireshark, tshark, tcpdump, Tips & Tricks, Notes, Network Security, Unix, Solaris, Firewalls, Cisco ASA, Cisco PIX, Checkpoint, Netscreen

Source Destination Summary -------------------------------------------------------------------------------------- [192.168.0.5] [192.168.0.3] TCP: D=80 S=44545 SYN SEQ=3017830046 LEN=0 WIN=4096 [192.168.0.3] [192.168.0.5] TCP: D=44545 S=80 RST ACK=3017830047 WIN=0



